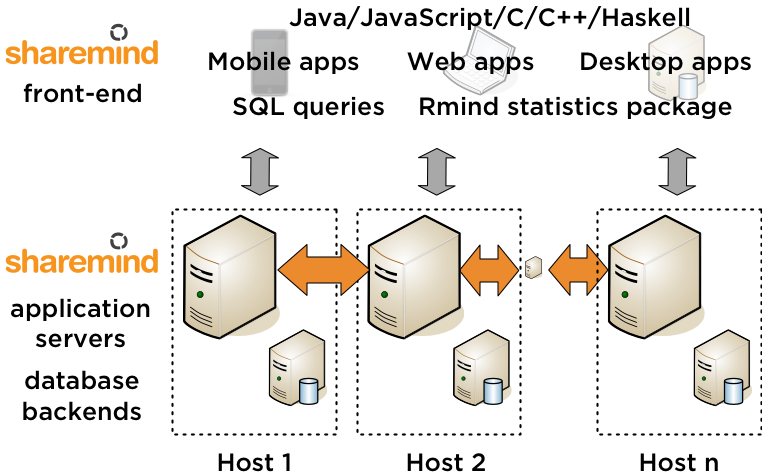
A Review Study on the Privacy Preserving Data Mining Techniques and Approaches | Manish Sharma and Manish Mathuria - Academia.edu
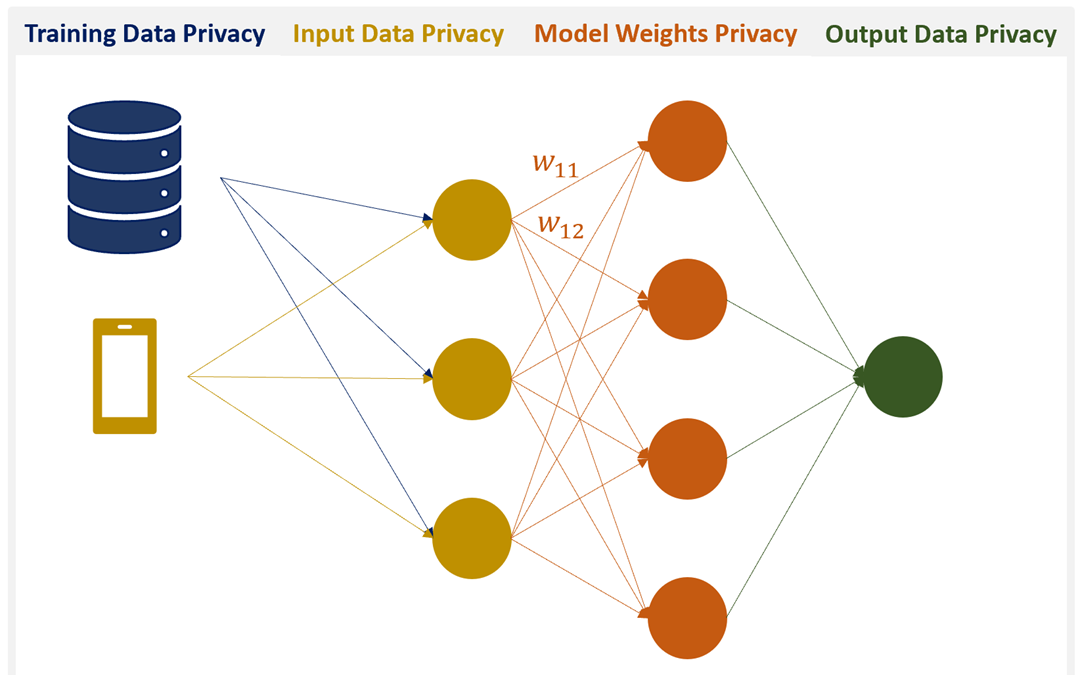
Perfectly Privacy-Preserving AI. What is it and how do we achieve it? | by Patricia Thaine | Towards Data Science
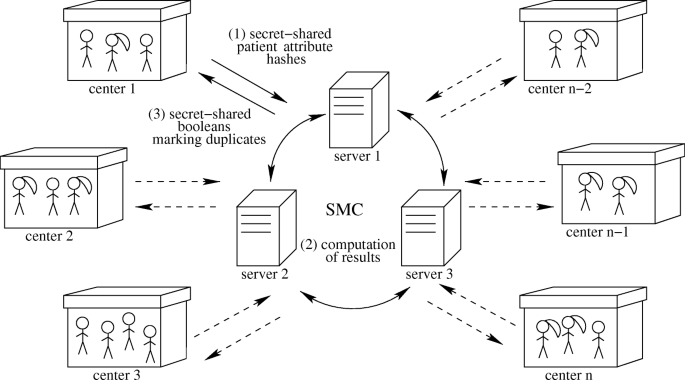
Privacy-preserving record linkage in large databases using secure multiparty computation | BMC Medical Genomics | Full Text

Analysis and Evaluation of Schemes for Secure Sum in Collaborative Frequent Itemset Mining across Horizontally Partitioned Data
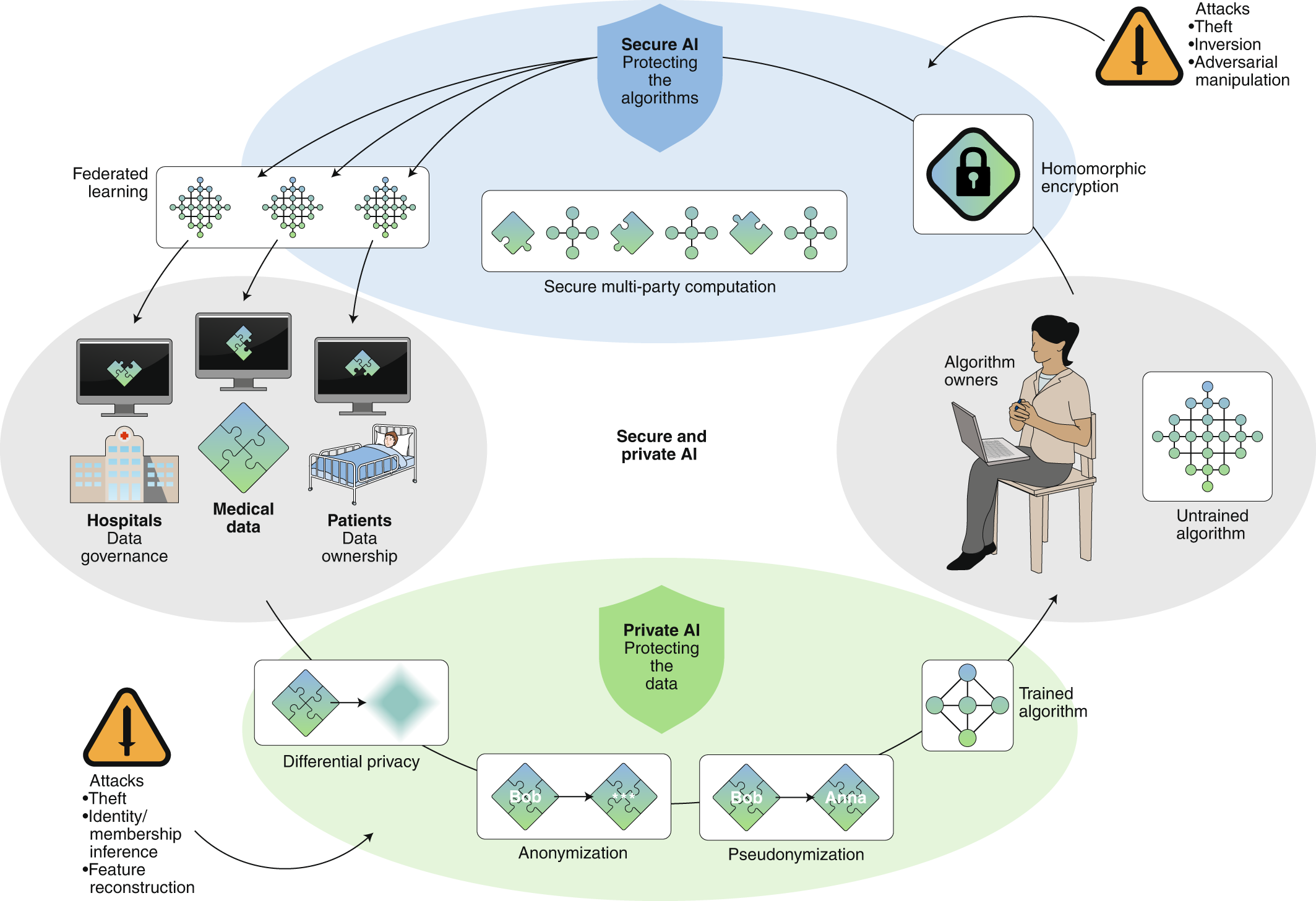
Secure, privacy-preserving and federated machine learning in medical imaging | Nature Machine Intelligence

Secure Multiparty Computation for Privacy Preserving Data Mining: Computer Science & IT Book Chapter | IGI Global

Li Xiong CS573 Data Privacy and Security Privacy Preserving Data Mining – Secure multiparty computation and random response techniques. - ppt download

Privacy Preserving Distributed Data Mining Based on Secure Multi-party Computation | Semantic Scholar
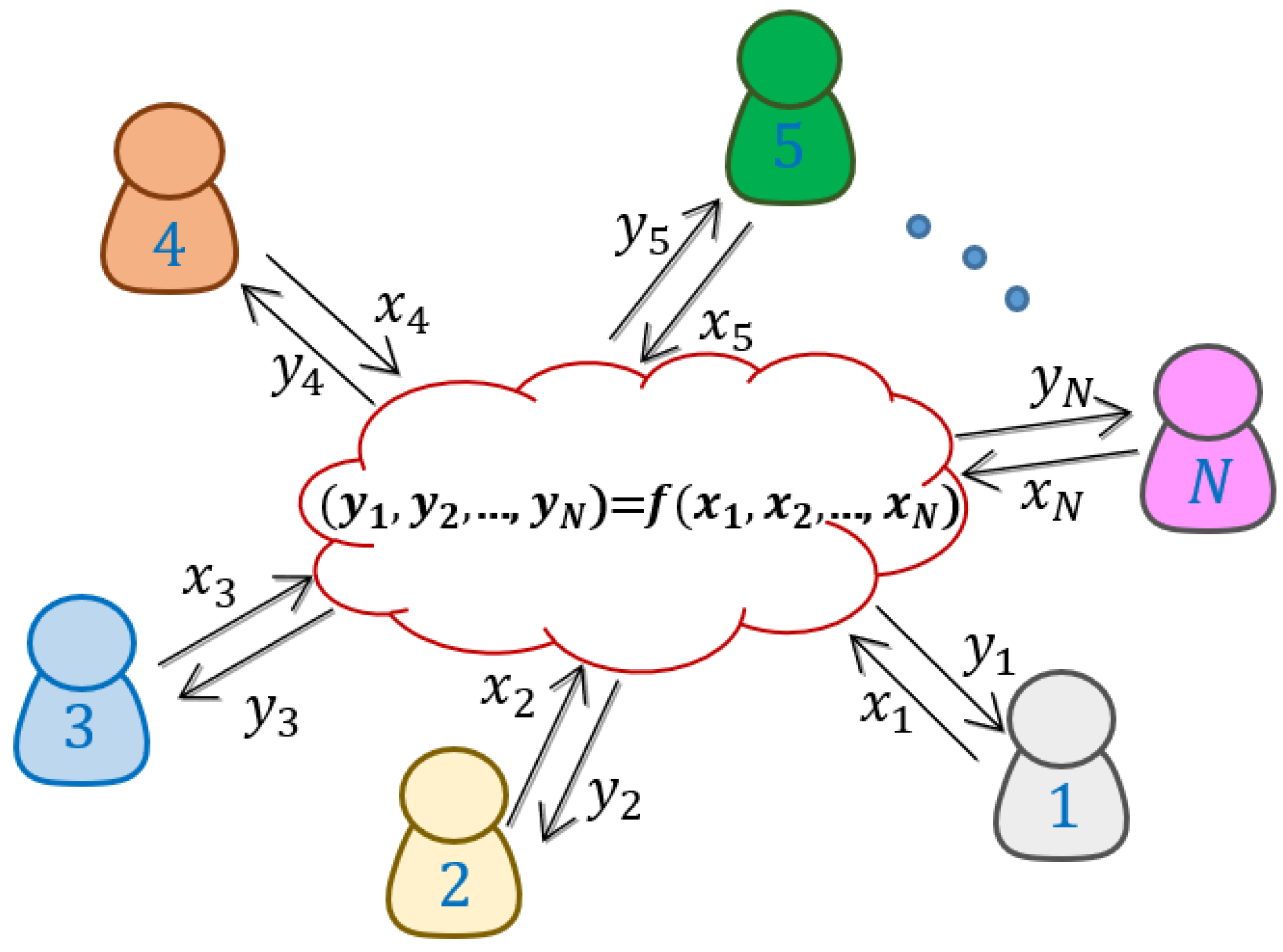
Applied Sciences | Free Full-Text | Generation and Distribution of Quantum Oblivious Keys for Secure Multiparty Computation
Privacy Preserving Medical Data Analytics using Secure Multi Party Computation. An End-To-End Use Case.
![PDF] Secure Multiparty Computation during Privacy Preserving Data Mining: Inscrutability Aided Protocol for Indian Healthcare Sector | Semantic Scholar PDF] Secure Multiparty Computation during Privacy Preserving Data Mining: Inscrutability Aided Protocol for Indian Healthcare Sector | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/54858338e517a3112133e7e664d762299842671b/5-Figure2-1.png)



![PDF] Secure Multiparty Computation for Privacy-Preserving Data Mining | Semantic Scholar PDF] Secure Multiparty Computation for Privacy-Preserving Data Mining | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/55682d5db7f02b99ee979c3cda256b5db494c6fb/2-Figure1-1.png)