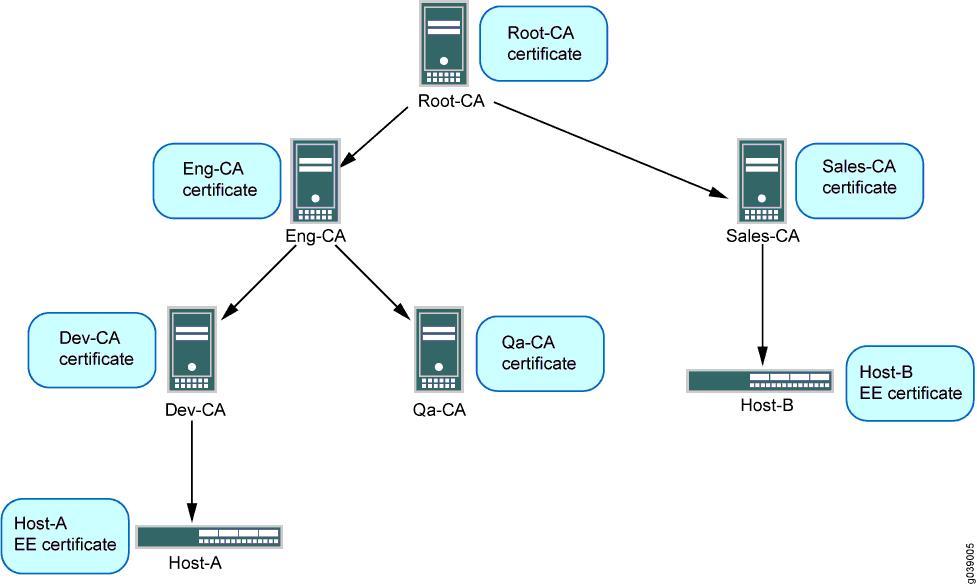
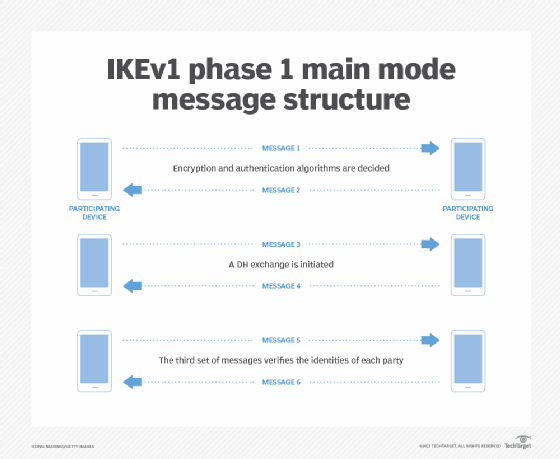
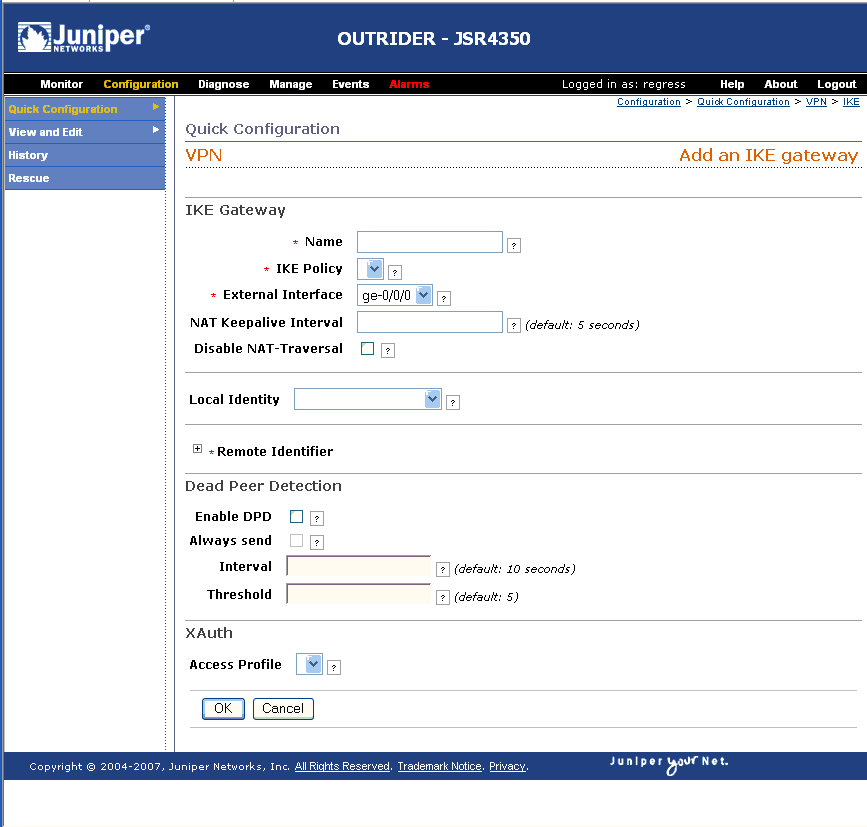
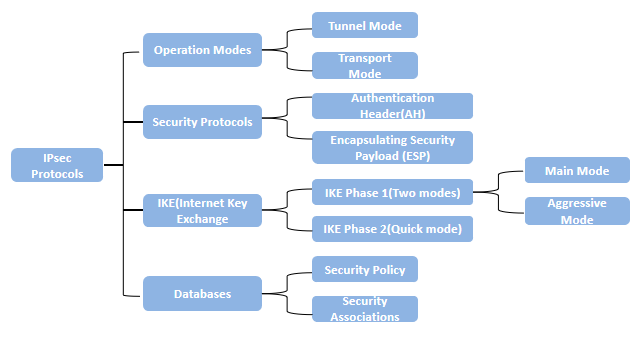
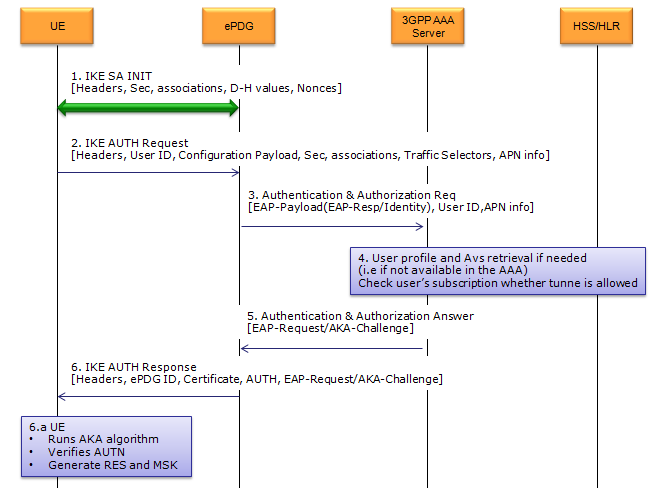
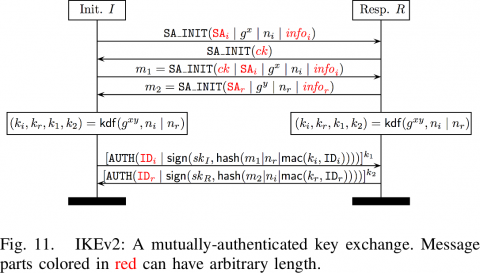
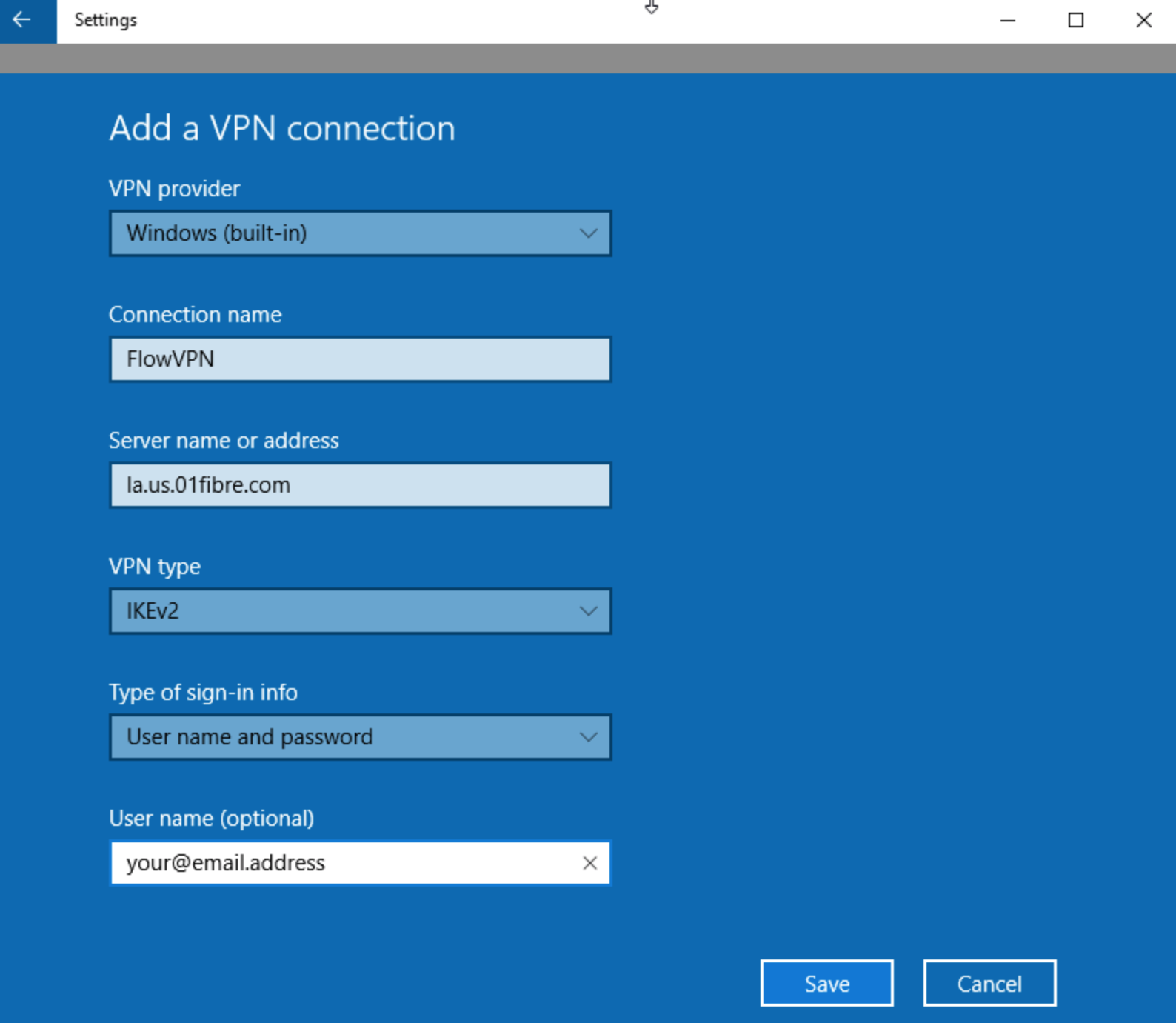
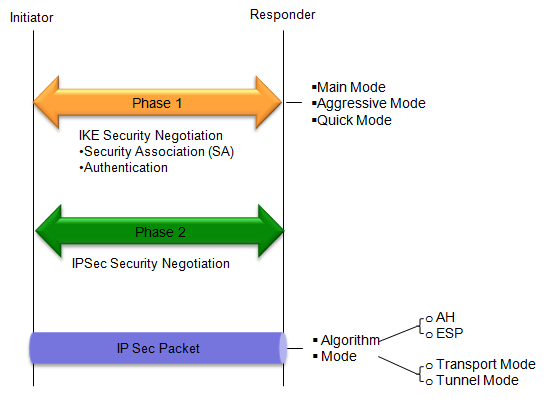
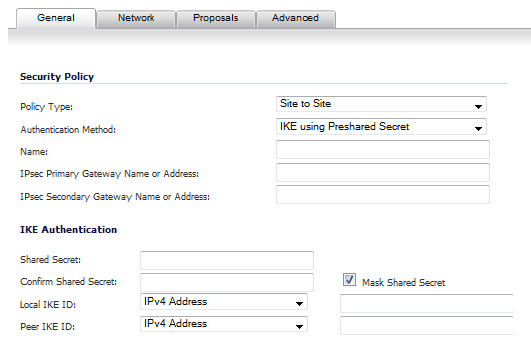
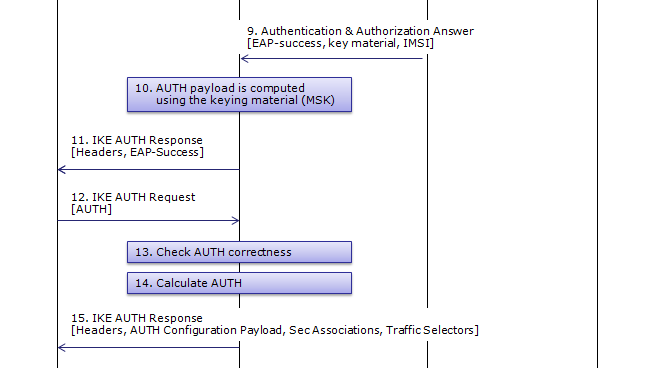
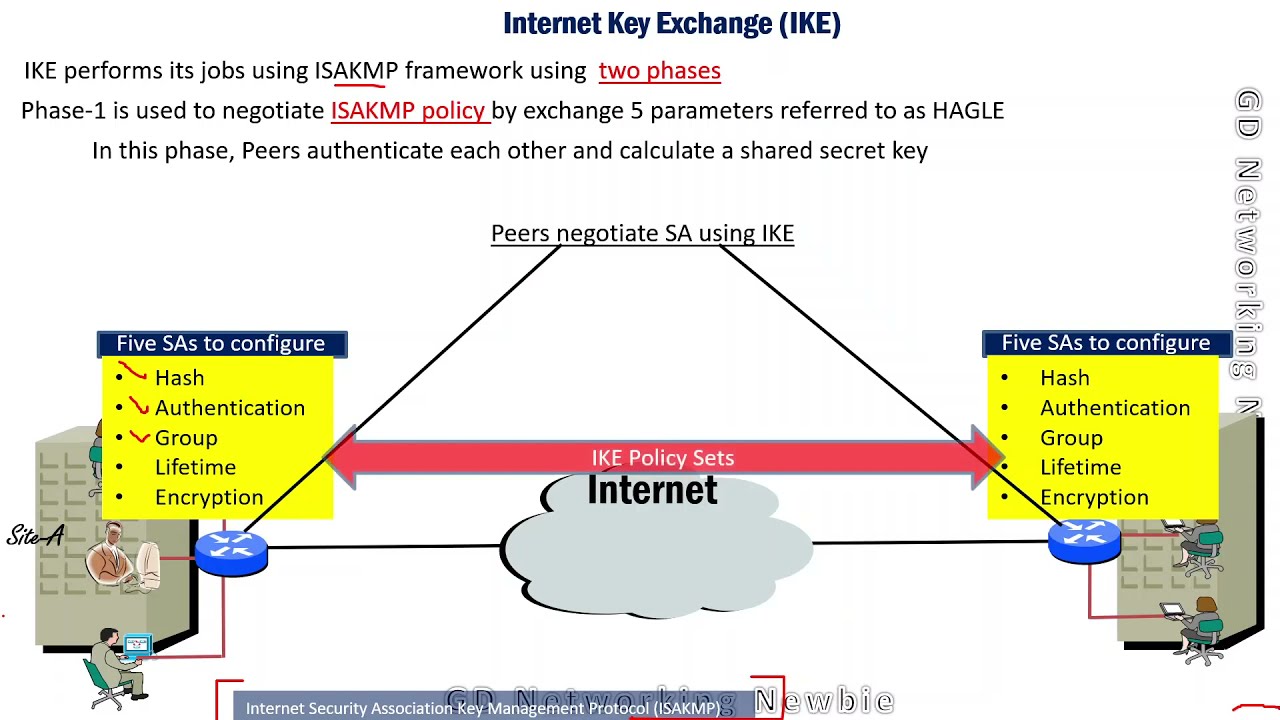
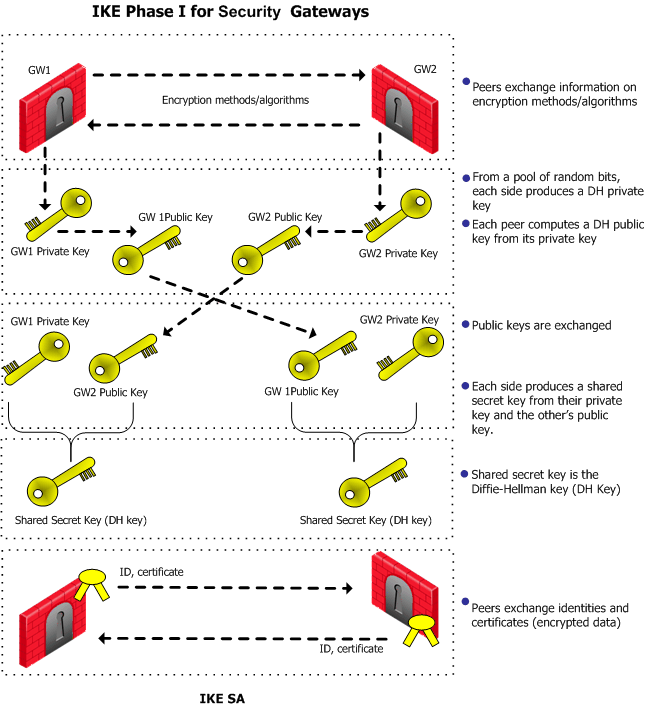
Pulse Secure Article: KB23221 - '13801: IKE authentication credentials are unacceptable' error message
How to Configure Certificate-Based Authentication for IKE on PA... - Knowledge Base - Palo Alto Networks
Datto Networking Appliance (DNA): "IKE Authentication Credentials Are Unacceptable" Error Message When Using Client VPN
![Configuring Cisco IOS Easy VPN Remote with 802.1x Authentication [IPSec Negotiation/IKE Protocols] - Cisco Systems Configuring Cisco IOS Easy VPN Remote with 802.1x Authentication [IPSec Negotiation/IKE Protocols] - Cisco Systems](https://www.cisco.com/en/US/technologies/tk583/tk372/images/09186a008065e3be_guest-IPSec-us-Technology_White_Paper-en_2_2-1.jpg)