Isometric Data Flow Processing Data Protection Encryption Process Server Room Stock Vector Image by ©modpic #196866632

Symmetry | Free Full-Text | Efficient Hierarchical Identity-Based Encryption System for Internet of Things Infrastructure

Google Boosting Encryption Between Data Centers | Data Center Knowledge | News and analysis for the data center industry

Equinix Pitches Single System for All Your Cloud Encryption Keys | Data Center Knowledge | News and analysis for the data center industry

Managing Encryption for Data Centers Is Hard. And It Will Get Harder | Data Center Knowledge | News and analysis for the data center industry
Center for Data Innovation - What Will Be the Impact of the UK's Online Safety Bill on Encryption and Anonymity Online? - Center for Democracy and Technology
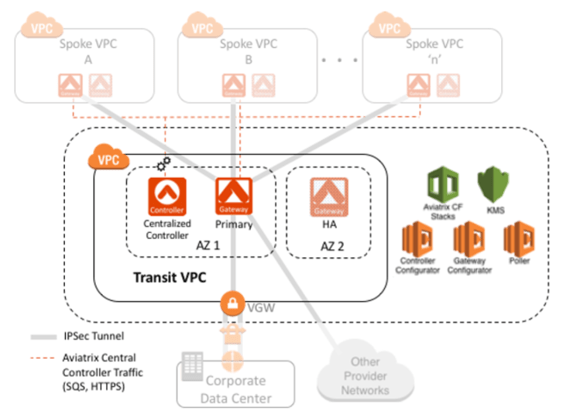
How should I encrypt data-in-motion between my data center and the AWS Global Transit VPC? - Aviatrix